Exploring the Evolution of Phishing
Most everyone has them lurking in their email — phishing attempts.
While spam filters often divert the deceitful messages away from your inbox, hackers have tried new strategies over the years to better conceal their fraudulence.
NC State doctoral student Olga Zielinska studies how phishing has evolved over time. Her current project, sponsored by the Science of Security Lablet at NC State, looks specifically at the various persuasive elements that hackers use to trick email filtering systems and users.
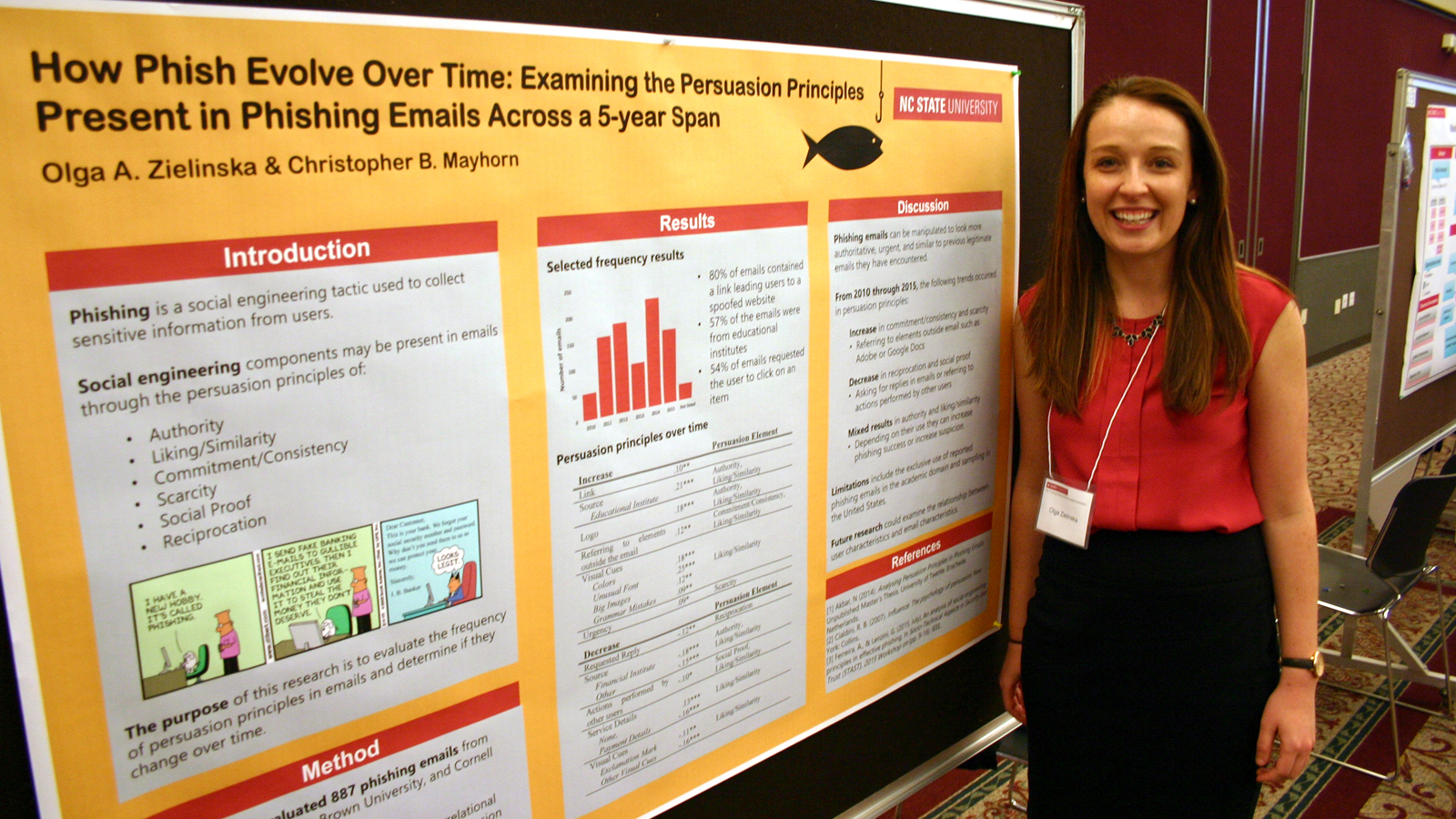
Zielinska, who is pursuing her Ph.D. in the Department of Psychology’s Human Factors and Applied Cognition program, recently presented findings from the study in a poster at the NC State Graduate Student Research Symposium. We caught up with her about the work and its significance in the field.
Q: It appears that your work with phishing stems back several years. What led you to pursue this area of research?
A: During my first few weeks of graduate school, my adviser, Dr. Christopher Mayhorn, invited me to a research planning meeting where they were discussing the next steps of a phishing study they were about to start. Three years and multiple research studies later, I am still hooked.
Q: How does this current project build on your previous work and other scholarship around phishing? What questions did you ask?
A: Phishing studies have focused on the behavior of the email receiver, such as ways to train users not to fall victim to phishing, what personality characteristics make people more vulnerable to phishing and cultural differences that could make certain individuals more susceptible; however, phishing is an interaction between two people: the hacker and the email receiver.
There have not been many studies examining what techniques hackers use to convince users to divulge the information. Unfortunately, we don’t have access to the hackers to ask them what their strategies are, but we do have access to a large database of emails they have sent. This current project focuses on the persuasive elements of the emails.
Q: How did you collect your data?
A: We collected emails available through phishing databases at Arizona State University, Brown University and Cornell University. There were 889 emails that spanned a five-year period, and they were classified by two research assistants through a questionnaire we adapted.
Q: What did you find?
A: Over the five-year span, there was an increase in emails that contained a link to click on and a decrease in emails that requested a reply. There was also an increase in the number of emails from academic sources and a decrease in email sources claiming to be from banks or other commonly used companies such as Microsoft or Google.
Additionally, there was an increase in a sense of urgency in the emails (i.e. must respond in 24 hours or less), a presence of logos to seem more legitimate and referring to elements outside the email (i.e. use Adobe PDF reader to access this document).
Overall, we suspect that phishers have found success obtaining information using certain email characteristics and not as much success using others, explaining the increase of certain attributes (i.e. emails from academic sources) and a decrease in other attributes (i.e. requesting a reply).
Q: What is the significance of these findings, for users and cybersecurity developers?
A: By understanding the characteristics of the phishing emails, we can develop more effective training programs for users and inform cybersecurity developers as they create anti-phishing software.
Q: In addition to the NC State Graduate Research Symposium, are you presenting these findings elsewhere? Do you plan to publish the results?
A: Yes, I will be presenting a poster at the Symposium and Bootcamp on the Science of Security during the third week of April, and I recently was accepted to present the findings during a talk at the Human Factors and Ergonomics Society Annual Meeting in Washington at the end of September.
Q: How have professors or experiences at NC State helped prepare you for research like this?
A: The interdisciplinary nature of the Science of Security Lablet helped expose me to the topic of phishing, the current cybersecurity research and the importance of understanding human behavior during this process. The professors provided interesting project ideas, valuable input and opportunities to publish and present this research at multiple conferences.
Q: What’s next for you after grad school?
A: I have had many great opportunities to work in academic settings as a teaching assistant and to work alongside the government with my current research assistantship through the Science of Security Lablet. This summer I will work in industry through an internship with Apple. I have enjoyed each of these experiences and learned a lot about working in each sector. At this time, I am focusing on completing my dissertation and keeping a lookout for potential opportunities that will open up in the next year.